Ransomware is a sophisticated and serious threat to your information system, and it can cost your business a lot. The good news is using the right controls and security approach you can defend against ransomware virus. Many service providers and software companies use scare tactics to drum up business. One of their favourite red flags is ransomware protection, and their solutions almost always incomplete and expensive. Some SMB owners, panicked by a potential ransomware attack, fold and crash their budgets to ward off security threats. Others, with limited resources, put their heads in the sand and pretend that their systems are safe. Both reactions defy logic and are not the way to go.
In this article, we outline a constructive self-help solution that:

In this article, we have delivered a complete solution to protect your system from a ransomware attack. Our multi-layered security solution is the only way to ensure your safety against a sophisticated ransomware attack. The rules of security engagement are clear:
Spam Emails are the number one source for spreading a ransomware virus. There are two methods of attack used by spammers:
Sophisticated hackers use OneDrive, Dropbox or Google Drive, and the like. They know that most companies see these cloud storage providers as high status and legitimate, allowing traffic in without too much scrutiny. For example, the hacker stores a malware file in Microsoft OneDrive and then shares that file via an OneDrive link in an email. From a deviousness point-of-view, it’s streets ahead of throwing out some random domain name and then hoping for the best.
In summary: Good spam protection reduces your exposure by blocking most of the phishing emails. Make sure that your spam protection is capable of performing SSL inspection and context-aware scanning to identify and block malicious links and domains.

Spam protection plays a vital role by blocking most of the malicious emails before they deliver to your end-users. But even the best spam filtering system fails to stop all spams messages. When end users accidentally click on destructive links in a spam email, then content filtering is your next line of defence. Content filtering use blacklists to block known malicious domains and perform a real-time malware scan on each file. It can scan encrypted content using SSL inspection, and utilise behaviour-based detection mechanisms to filter internet traffic.
Spam protection and content filtering, in combination, stop the majority of the ransomware attacks. However, it’s not perfect. Carefully crafted malware attacks can bypass both spam and content filtering. The malware could also introduce to your network from other means like removable storage devices. Here’s the thing: it only takes one to spiral things out of control. If the ransomware virus reached your network, you have to be ready to counteract it. Antivirus is the next preventative control that you should have installed, configured, and prepared to spring into action.
Behaviour-Based scan capabilities, in addition to malware signatures – it’s impossible to have signatures for all malware. A behaviour-based feature is invaluable because it defends against newly released viruses and zero-day threats even when the signatures are not available in its database. It’s especially pertinent when it comes to ransomware popping up new strings frequently. For example, a behaviour base antivirus can detect if a process is trying to encrypt multiple files, hence terminating the process quickly.
Antivirus must have an application control feature – It exerts essential, tighter control over end-user execution rights by restricting the installation of unauthorised software. Application control policies are necessary to stop ransomware from causing damage by:
We are a big fan of Trend Micro and Sophos Antivirus. These products have a low footprint on the system resources and tick all the boxes when it comes to defending against ransomware. Depending on the size and need of your business, you can choose between different product versions. For example:
Speak with our support team to get your no-obligation Antivirus configuration and policy check today. The iVersion ransomware experts go substantially further than others, and we do it without disrupting affordability.
Here are some eye-popping facts:
Therefore, we advise, limiting write access to the network files and folders on a need-to-know basis. It’ll help prevent unauthorised data deletion and changes while containing the damage a ransomware virus can cause. In short, this simple step severely reduces the impact of a viral attack against your network.
We tell all our clients to prepare for the worst while doing everything in their power to achieve the best. So, that said, are you ready to deal with a ransomware disaster?
Windows Shadow Copy is one of the cheapest controls available to most users, even individuals working from home. There’s no cost associated with it if you have a professional or enterprise version of the Windows operating system. Yet, we see most of the businesses in Australia missing this control. Windows Shadow Copy on the computers and servers volumes makes your recovery effort fast and straightforward.
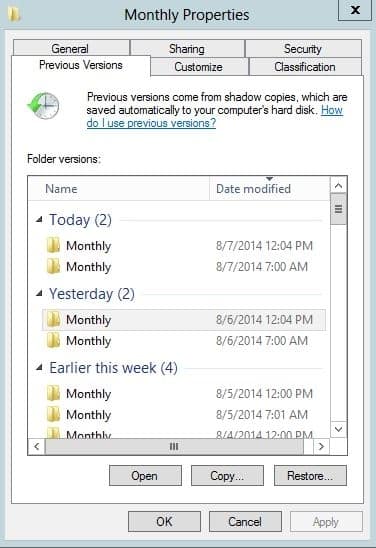
Not having a regular backup is a recipe for disaster.
Be prepared and know how to act during and after an incident. Your incident response policy and procedures should be clear, and it must include:
You can pinpoint the source of infection using the following:
If you want to stay one step ahead of ransomware, use the do-it-yourself list above or call Australia’s leading ransomware consultant. For more information or quick complimentary ransomware, preparation check do not hesitate to contact us on 1800 864 868
Get the Right People to Manage your IT
Sign Up and Stay Informed